Recognition model of IIoT equipment in coal mine
-
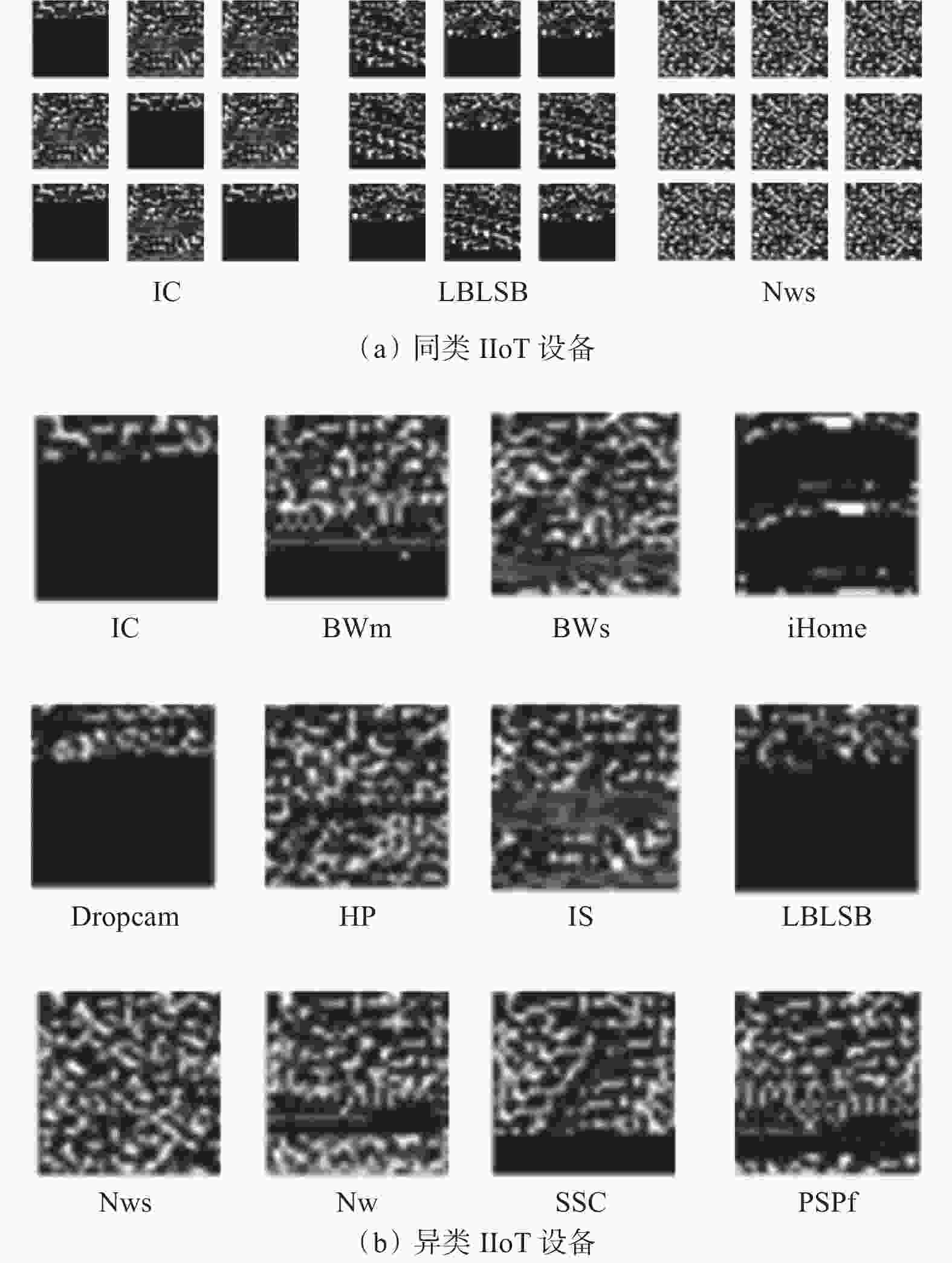
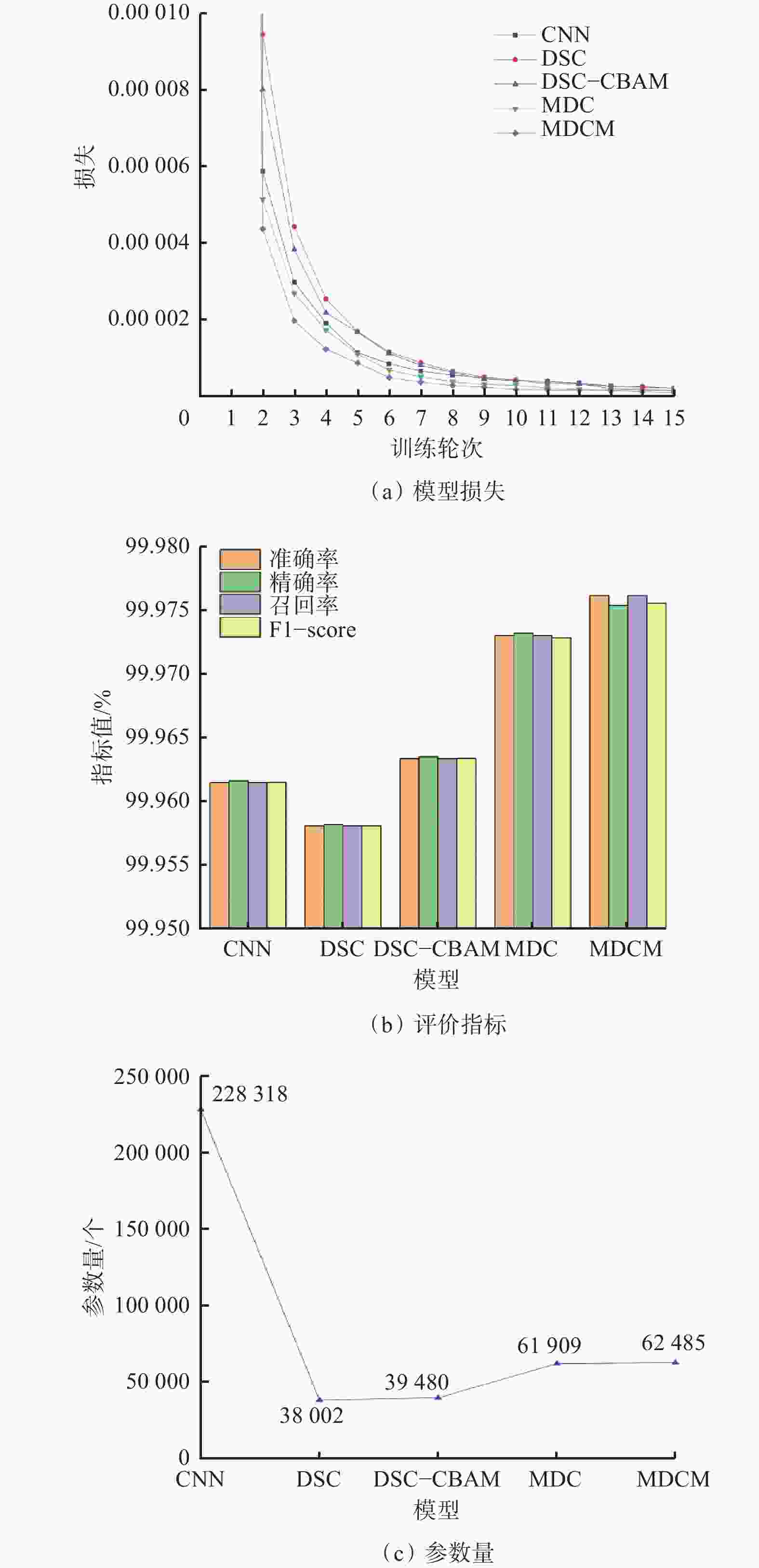
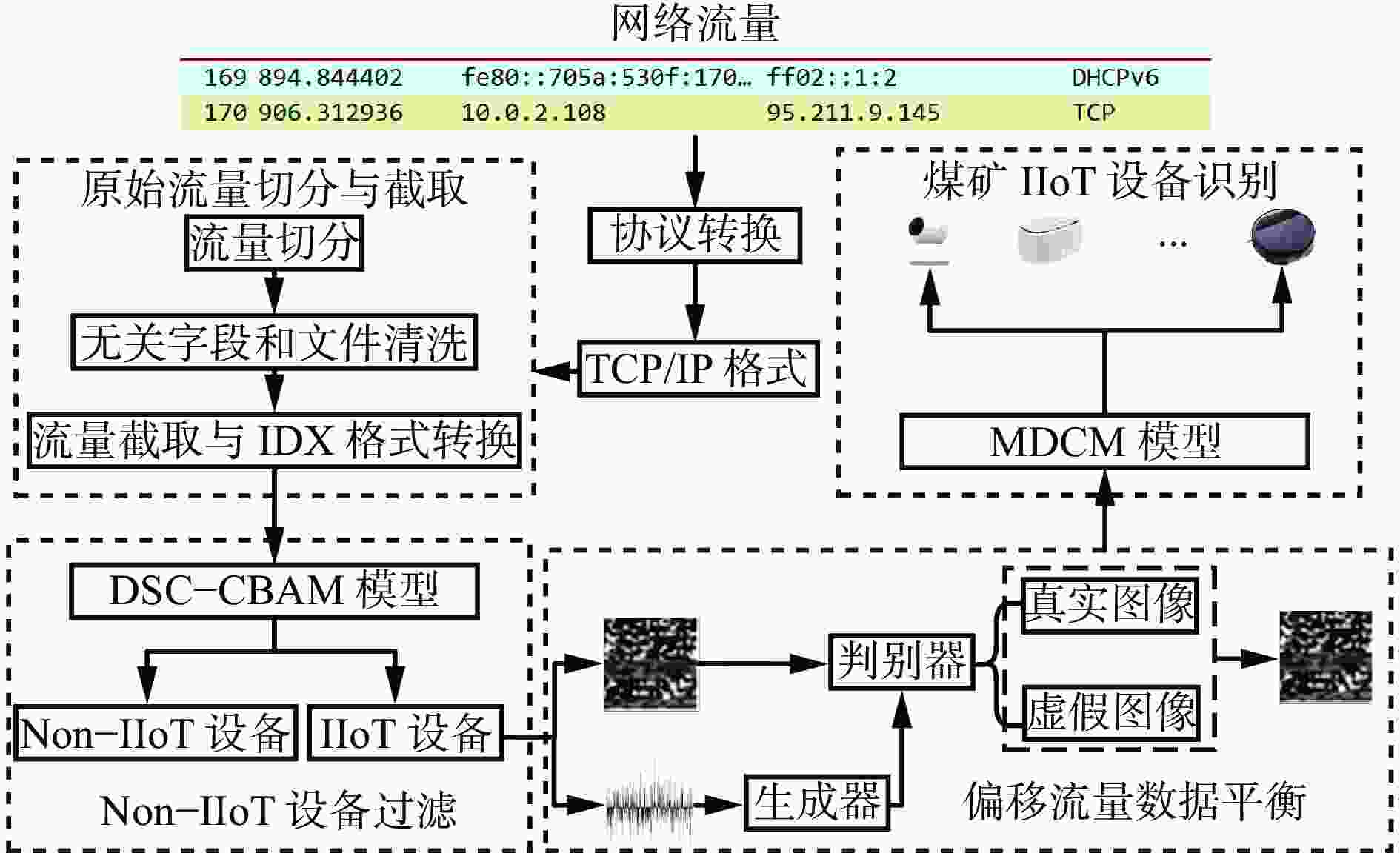
摘要: 煤矿工业物联网(IIoT)设备计算与存储资源受限,易遭受非法网络入侵,造成敏感数据泄露或恶意篡改,威胁煤矿生产安全。精准识别煤矿IIoT设备可实现有效管理并维护设备正常运转,提高设备安全防护能力,然而现有设备识别算法存在特征构造复杂、内存与计算需求较高导致难以部署在资源受限的煤矿IIoT设备中等问题。针对上述问题,提出了一种煤矿IIoT设备识别模型。首先,对支持TCP/IP协议传输的流量数据进行流量切分、无关字段去除、去重、定长字段截取操作后转换为IDX格式存储;其次,使用卷积块注意力模块(CBAM)优化深度可分离卷积(DSC),从而搭建轻量级DSC−CBAM模型来过滤Non−IIoT设备;然后,利用带有阶段惩罚的Wasserstein生成对抗网络(WGAN−GP)扩充流量较少的煤矿IIoT设备数据,达到平衡偏移流量数据的目的;最后,在DSC−CBAM基础上引入多尺度特征融合(MFF)技术捕获浅层全局特征信息,并增加Mish激活函数提高模型训练稳定性,建立优化混合模态识别(MDCM)模型,实现煤矿IIoT设备精准识别。实验结果表明,该模型收敛速度快,准确率、召回率、精确率与F1−score指标均高达99.98%,且参数量小,能精准、高效识别煤矿IIoT设备。Abstract: The computing and storage resources of the industrial Internet of things (IIoT) equipment in the coal mine are limited, making it vulnerable to illegal network intrusion, causing sensitive data leakage or malicious tampering, and threatening the safety of coal mine production. Precise recognition of coal mine IIoT equipment can achieve effective management and maintenance of equipment operation, improve equipment safety and protection capabilities. However, existing equipment recognition algorithms suffer from complex feature construction, high memory and computing requirements, making it difficult to deploy in resource limited coal mine IIoT equipment. In order to solve the above problems, a coal mine IIoT equipment recognition model is proposed. Firstly, the model performs traffic segmentation, irrelevant field removal, deduplication, and fixed length field truncation operations on traffic data that supports TCP/IP protocol transmission. The model then converts it to IDX format for storage. Secondly, the model uses convolutional block attention module (CBAM) to optimize depthwise separable convolu-tion(DSC). A lightweight DSC-CBAM model is constructed to filter Non-IIoT equipment. Thirdly, the Wasserstein generative adversarial network with gradient penalty (WGAN-GP) is used to expand the data of coal mine IIoT equipment with less traffic, achieving the goal of balancing offset traffic data. Finally, multi-scale feature fusion (MFF) technology is introduced on the basis of DSC-CBAM to capture shallow global feature information, and Mish activation function is added to improve model training stability. The MFF-DSC-CBAM-Mish (MDCM) model is established to achieve precise recognition of coal mine IIoT equipment. The experimental results show that the model has a fast convergence speed, with accuracy, recall, precision, and F1 score all reaching 99.98%. The model has a small number of parameters, which can accurately and efficiently recognize IIoT equipment in coal mines.
-
表 1 MDCM模型网络结构
Table 1. Network structure of MDCM model
网络层 输出尺寸 卷积核参数 输入层 1×28×28 — MFF卷积层1 16×28×28 3×3,16个 MFF卷积层2 16×28×28 5×5,16个 池化层1 32×14×14 2×2 DW层1 32×12×12 3×3,32个 CBAM层1 32×12×12 — PW层1 64×12×12 1×1,64个 DW层2 64×10×10 3×3,64个 CBAM层2 64×10×10 — PW层2 16×10×10 1×1,16个 池化层2 16×5×5 2×2 全连接层 128 — 输出层 26 — 表 2 Non−IIoT设备过滤结果对比
Table 2. Comparison of filtering results of Non-IIoT equipment
表 3 偏移流量数据平衡前后设备识别指标对比
Table 3. Comparison of equipment recognition indicators before and after offset flow data balancing
% IIoT设备 精确率 召回率 F1−score 平衡前 平衡后 平衡前 平衡后 平衡前 平衡后 Ae 100 100 99.99 100 99.99 100 BWms 99.95 100 100 99.98 99.98 99.99 BWs 99.99 99.99 99.99 99.99 99.99 99.99 BBPm 100 100 50.00 100 66.67 100 Dropcam 96.15 100 100 100 98.04 100 HP−Printer 99.67 99.33 100 99.66 99.83 99.50 iHome 100 100 100 100 100 100 IC 99.99 99.99 99.97 100 99.98 100 LBLSB 100 100 100 100 100 100 ND 100 100 100 99.50 100 99.75 NPsa 96.67 99.50 96.67 100 96.67 99.75 Nws 100 100 100 100 100 100 NW 100 100 100 100 100 100 PSPf 99.92 100 100 100 99.96 100 SS 100 99.98 99.95 99.98 99.98 99.98 ST 100 100 99.92 100 99.96 100 TDNCc 100 100 100 100 100 100 TSp 99.62 100 100 100 99.81 100 TRBL 99.92 99.90 99.97 99.92 99.95 99.91 TS 100 100 100 99.50 100 99.75 WAsss 0 100 0 100 0 100 WSBM 0 100 0 100 0 100 WSs 87.50 100 100 100 93.33 100 HB 100 100 99.59 99.59 99.80 99.80 HC 99.41 99.55 100 99.12 99.71 99.18 DLDS 100 100 95.83 98.49 97.87 99.24 -
[1] 李首滨,刘道园. 基于工业互联网的智能矿山研究与设计[J]. 中国煤炭,2021,47(2):59-65.LI Shoubin,LIU Daoyuan. Research and design of intelligent mine based on industrial Internet[J]. China Coal,2021,47(2):59-65. [2] HAO Qinxia,RONG Zheng. IoTTFID:an incremental IoT device identification model based on traffic fingerprint[J]. IEEE Access,2023,11:58679-58691. doi: 10.1109/ACCESS.2023.3284542 [3] LIU Jie,SUN Yi,XU Fengkai,et al. IIS:intelligent identification scheme of massive IoT devices[C]. IEEE 45th Annual Computers,Software,and Applications Conference,Madrid,2021:1623-1626. [4] ZHOU Feng,QU Hua,LIU Hailong,et al. Fingerprinting IIoT devices through machine learning techniques[J]. Journal of Signal Processing Systems,2021,93:779-794. doi: 10.1007/s11265-021-01656-0 [5] MIETTINEN M,MARCHAL S,HAFEEZ I,et al. IoT sentinel:automated device-type identification for security enforcement in IoT[C]. IEEE 37th International Conference on Distributed Computing Systems,Atlanta,2017:2177-2184. [6] SIVANATHAN A,GHARAKHEILI H H,LOI F,et al. Classifying IoT devices in smart environments using network traffic characteristics[J]. IEEE Transactions on Mobile Computing,2018,18(8):1745-1759. [7] MAHESH B. Machine learning algorithms-a review[J]. International Journal of Science and Research,2020,9(1):381-386. [8] ALZUBAIDI L,ZHANG Jinglan,HUMAIDI A J,et al. Review of deep learning:concepts,CNN architectures,challenges,applications,future directions[J]. Journal of Big Data,2021,8:1-74. doi: 10.1186/s40537-020-00387-6 [9] ORTIZ J,CRAWFORD C,LE F. DeviceMien:network device behavior modeling for identifying unknown IoT devices[C]. International Conference on Internet of Things Design and Implementation,Montreal,2019:106-117. [10] YIN Feihong,YANG Li,WANG Yuchen,et al. IoT ETEI:end-to-end IoT device identification method[C]. IEEE Conference on Dependable and Secure Computing,Aizuwakamatsu,2021:1-8. [11] KOTAK J,ELOVICI Y. IoT device identification based on network communication analysis using deep learning[J]. Journal of Ambient Intelligence and Humanized Computing,2023,14(7):9113-9129. doi: 10.1007/s12652-022-04415-6 [12] KRIZHEVSKY A,SUTSKEVER I,HINTON G E. ImageNet classification with deep convolutional neural networks[J]. Advances in neural information processing systems,2012,25(2). DOI: 10.1145/3065386. [13] HOWARD A,SANDLER M,CHEN Bo,et al. Searching for mobileNetV3[C]. IEEE/CVF International Conference on Computer Vision,Seoul,2019:1314-1324. [14] ELSKEN T,METZEN J H,HUTTER F. Neural architecture search:a survey[J]. Journal of Machine Learning Research,2019,20(55):1-21. [15] HAN Song,MAO Huizi,DALLY W J. Deep compression:compressing deep neural networks with pruning,trained quantization and Huffman coding[J]. Fiber,2015,56(4):3-7. [16] HAN Song,POOL J,TRAN J,et al. Learning both weights and connections for efficient neural network[J]. Advances in Neural Information Processing Systems,2015. DOI: 10.48550/arXiv.1506.02626. [17] 王军,冯孙铖,程勇. 深度学习的轻量化神经网络结构研究综述[J]. 计算机工程,2021,47(8):1-13.WANG Jun,FENG Suncheng,CHENG Yong. Survey of research on lightweight neural network structures for deep learning[J]. Computer Engineering,2021,47(8):1-13. [18] WOO S,PARK J,LEE J Y,et al. CBAM:convolutional block attention module[C]. European Conference on Computer Vision,Munich,2018:3-19. [19] GULRAJANI I,AHMED F,ARJOVSKY M,et al. Improved training of Wasserstein GANs[J]. Advances in Neural Information Processing Systems,2017. DOI: 10.48550/arXiv.1704.00028. [20] DUBEY S R,SINGH S K,CHAUDHURI B B. Activation functions in deep learning:a comprehensive survey and benchmark[J]. Neurocomputing,2022,503:92-108. doi: 10.1016/j.neucom.2022.06.111 [21] WANG Wei,ZHU Ming,WANG Jinlin,et al. End-to-end encrypted traffic classification with one-dimensional convolution neural networks[C]. IEEE International Conference on Intelligence and Security Informatics,Beijing,2017:43-48. [22] 王伟. 基于深度学习的网络流量分类及异常检测方法研究[D]. 合肥:中国科学技术大学,2018.WANG Wei. Deep learning for network traffic classification and anomaly detection[D]. Hefei:University of Science and Technology of China,2018. [23] WANG Wei,ZHU Ming,ZENG Xuewen,et al. Malware traffic classification using convolutional neural network for representation learning[C]. International Conference on Information Networking,Da Nang,2017:712-717. [24] KOUKIS D,ANTONATOS S,ANTONIADES D,et al. A generic anonymization framework for network traffic[C]. IEEE International Conference on Communications,Istanbul,2006:2302-2309. [25] WANG Wei,SHENG Yiqiang,WANG Jinlin,et al. HAST-IDS:learning hierarchical spatial-temporal features using deep neural networks to improve intrusion detection[J]. IEEE Access,2017,6:1792-1806. [26] FAN Linna,HE Lin,DONG Enhuan,et al. EvoIoT:an evolutionary IoT and non-IoT classification model in open environments[J]. Computer Networks,2022,219. DOI: 10.1016/j.comnet.2022.109450. [27] 孙洁娣,王利轩,温江涛,等. 改进稠密块轻量化神经网络的管道泄漏孔径识别[J]. 仪器仪表学报,2022,43(3):98-108.SUN Jiedi,WANG Lixuan,WEN Jiangtao,et al. Pipeline leakage aperture recognition based on lightweight neural network with the improved dense block[J]. Chinese Journal of Scientific Instrument,2022,43(3):98-108. [28] HU Jie,SHEN Li,SUN Gang. Squeeze-and-excitation networks[C]. IEEE/CVF Conference on Computer Vision and Pattern Recognition,Salt Lake City,2018:7132-7141. [29] WANG Qilong,WU Banggu,ZHU Pengfei,et al. ECA-Net:efficient channel attention for deep convolutional neural networks[C]. IEEE/CVF Conference on Computer Vision and Pattern Recognition,Seattle,2020:11534-11542. [30] HU Jie,SHEN Li,ALBANIE S,et al. Gather-excite:exploiting feature context in convolutional neural networks[J]. Advances in Neural Information Processing Systems,2018. DOI: 10.48550/arXiv.1810.12348. [31] LI Xiang,WANG Wenhai,HU Xiaolin,et al. Selective kernel networks[C]. IEEE/CVF Conference on Computer Vision and Pattern Recognition,Long Beach,2019:510-519. [32] SANDLER M,HOWARD A,ZHU Menglong,et al. MobileNetV2:inverted residuals and linear bottlenecks[C]. IEEE Conference on Computer Vision and Pattern Recognition,Salt Lake City,2018:4510-4520. [33] THOUTI S,VENU N,RINKU D R,et al. Investigation on identify the multiple issues in IoT devices using convolutional neural network[J]. Measurement:Sensors,2022. DOI: 10.1016/j.measen.2022.100509. [34] 何志敏. 基于网络流量的物联网设备识别技术研究[D]. 南京:南京邮电大学,2022.HE Zhimin. Research on IoT device identification method based on network traffic[D]. Nanjing:Nanjing University of Posts and Telecommunications,2022. -
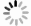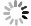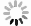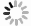



 下载:
下载: